ModSecurity is a tool that will filter malicious web server requests. DirectAdmin offers a graphical user interface where you can see the blocked requests for your sites or you can disable rules.
Sometimes there are false positives, so you may want to disable a few rules.
How to disable a ModSecurity rule in DirectAdmin:
1. Log into DirectAdmin account
2. Go to Advanced Features >> ModSecurity
3. On the Status & Disabled Rules tab, enter the rule(s) that you want to disable.
4. Click the DISABLE RULE button. The rule is disable now. ModSecurity will not block any longer requests that were triggered by the rule(s).
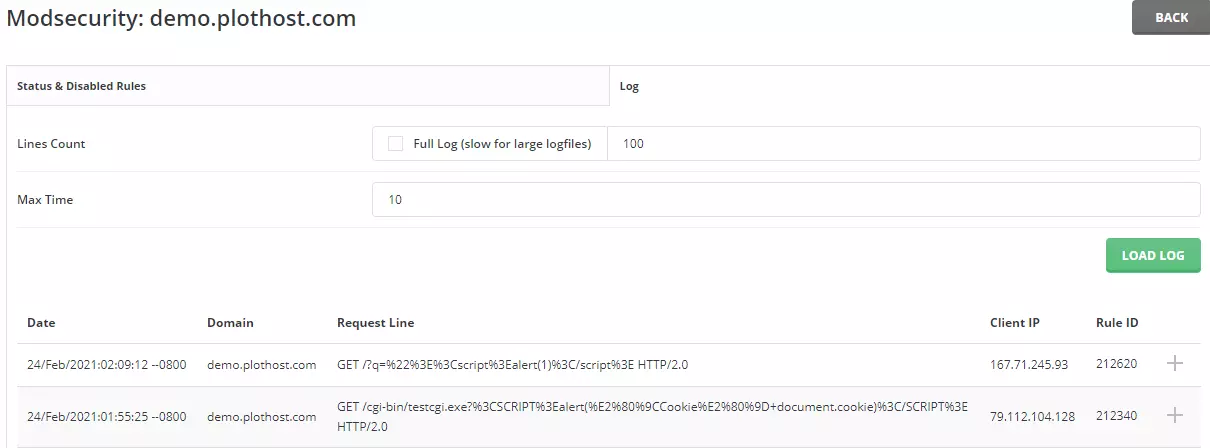
If you don’t know exactly what rule you should disable, check the logs on the second tab of the interface – the Log tab. You will see here the log of blocked requests. If you see legitimate requests, you can note the Rule ID number and remove it as explained above.
On the Log tab, you can also see details about blocked requests. For example:
{
"transaction": {
"time": "24/Feb/2021:02:09:12 --0800",
"transaction_id": "YDYlyHkMSWLizjeUPJz5dgAAG0g",
"remote_address": "167.71.245.93",
"remote_port": 52812,
"local_address": "209.141.49.206",
"local_port": 443
},
"request": {
"request_line": "GET /?q=%22%3E%3Cscript%3Ealert(1)%3C/script%3E HTTP/2.0",
"headers": {
"Sec-Ch-Ua": "\"Chromium\";v=\"88\", \"Google Chrome\";v=\"88\", \";Not A Brand\";v=\"99\"",
"Sec-Ch-Ua-Mobile": "?0",
"Upgrade-Insecure-Requests": "1",
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.182 Safari/537.36",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9",
"Sec-Fetch-Site": "none",
"Sec-Fetch-Mode": "navigate",
"Sec-Fetch-User": "?1",
"Sec-Fetch-Dest": "document",
"Accept-Encoding": "gzip, deflate, br",
"Accept-Language": "en-US,en;q=0.9,ro;q=0.8,he;q=0.7",
"Host": "demo.plothost.com"
}
},
"response": {
"protocol": "HTTP/1.1",
"status": 403,
"headers": {
"Content-Length": "199",
"Connection": "close",
"Content-Type": "text/html; charset=iso-8859-1"
},
"body": ""
},
"audit_data": {
"messages": [
"Access denied with code 403 (phase 2). Pattern match \"<script\\\\b\" at REQUEST_URI. [file \"/usr/local/cwaf/rules/07_XSS_XSS.conf\"] [line \"99\"] [id \"212620\"] [rev \"3\"] [msg \"COMODO WAF: Cross-site Scripting (XSS) Attack||demo.plothost.com|F|2\"] [data \"Matched Data: <script found within REQUEST_URI: /?q=\\x22><script>alert(1)</script>\"] [severity \"CRITICAL\"] [tag \"CWAF\"] [tag \"XSS\"]"
],
"error_messages": [
"[file \"apache2_util.c\"] [line 271] [level 3] [client 167.71.245.93] ModSecurity: Access denied with code 403 (phase 2). Pattern match \"<script\\\\\\\\\\\\\\\\b\" at REQUEST_URI. [file \"/usr/local/cwaf/rules/07_XSS_XSS.conf\"] [line \"99\"] [id \"212620\"] [rev \"3\"] [msg \"COMODO WAF: Cross-site Scripting (XSS) Attack||demo.plothost.com|F|2\"] [data \"Matched Data: <script found within REQUEST_URI: /?q=\\\\\\\\x22><script>alert(1)</script>\"] [severity \"CRITICAL\"] [tag \"CWAF\"] [tag \"XSS\"] [hostname \"demo.plothost.com\"] [uri \"/\"] [unique_id \"YDYlyHkMSWLizjeUPJz5dgAAG0g\"]"
],
"action": {
"intercepted": true,
"phase": 2,
"message": "Pattern match \"<script\\\\b\" at REQUEST_URI."
},
"stopwatch": {
"p1": 315,
"p2": 670,
"p3": 0,
"p4": 0,
"p5": 26,
"sr": 0,
"sw": 0,
"l": 0,
"gc": 0
},
"response_body_dechunked": true,
"producer": [
"ModSecurity for Apache/2.9.3 (http://www.modsecurity.org/)",
"CWAF_Nginx"
],
"server": "Apache/2",
"engine_mode": "ENABLED"
}
}The interface offers the possibility to switch SecRuleEngine ON or OFF. If you switch it to OFF, ModSecurity will be disabled totally. No rules will be processed. We do not recommend such an action.
We also made a video tutorial for this article:
